Originally published at: https://tidbits.com/2019/07/09/zoom-and-ringcentral-exploits-allows-remote-webcam-access/
Video conference systems Zoom and RingCentral have major vulnerabilities that could trigger your Web cam without permission. Here’s how to patch it yourself.
Thanks for bringing us the solution for this! I use it weekly for a class I teach, and it has worked really well. I have always hosted, though, never joined someone else’s session. All of the specifics and instructions in your article made perfect sense, but when I came to this sentence…
I’m able to still join conferences, but you may have to install the client yourself before joining a conference (the horror!)
I guess I’m reading it wrong, but I’m left asking, “Does Josh mean ‘If you’ve never used Zoom, you may have to install the app but then disable part of it by following these instructions; just using your regular browser won’t/may not work’?”
Thanks again.
Zoom has updated its statement, and is now rushing out an update that will remove the Web server. We’ll update our instructions when that happens.
The purpose of the Web server is to reinstall the client if you’ve uninstalled it, so you may have to take a few more steps to join a conference if you’ve uninstalled the app. I’d rewrite it to be clearer, but when Zoom updates the app to remove the Web server I’ll have to rewrite the article anyway, so…
Blue Jeans uses the same nonsense, and the app has not been updated to remove it (so far, from what I can see):
https://support.bluejeans.com/s/article/BlueJeans-Detector-Service
All of the terminal commands are a bit of overkill; there’s a much simpler way to deal with this. Go to System Preferences --> Users & Groups --> Login Items. You’ll see “Zoom Opener” listed there - just select it and click the “-” to delete it. Then log out or restart your Mac. That will stop the background server from running automatically, but the file will still be in a hidden “.zoomus” folder (to delete that, the terminal command is still useful, but it won’t do anything if you leave it there).
Zoom has released a new version of its client, version 4.4.4 (53932.0709), which offers a complete uninstall option and ditches the hidden server. I’ve update the article to reflect that update, but I’ve left the Terminal commands for historical reference and in case another bad app pulls a similar stunt.
Or in case, for some unfathomable reason, people are reluctant to download and install yet more software from these known purveyors of malware.
Fool me once…
Now Apple has joined in on the fun, releasing a silent update to kill the Zoom Web server. I’ve updated the article again to reflect that.
I’ve updated the article AGAIN to add more information about the stealth Apple update, and to add instructions from Karan Lyons on how to mitigate the vulnerability in Chrome and Firefox. Really, I just advise updating the Zoom client and uninstalling it entirely, it’ll save you a lot of trouble.
While the second of Leitschuh’s proof of concept links works and dumps me into the conference (audio/video initially both off as set in prefs), the first link just leads me to a page with broken image link. ![]()
Apple has released a second silent update to address vulnerabilities in RingCentral and Zhumu, the Chinese version of Zoom.
And with Zoom already showing incredibly poor judgment, we advise uninstalling the client unless you absolutely need it.
Just wondering, what app would you suggest for duplicating Zoom’s functionality?
Howard Oakley has penned a nice article about how to check that Zoom is really gone.
Since I read your article, I’ve been checking the System Information app’s “Installations” list, but the “MRTConfigData” item still says “1.28, 2018/01/27, 15:59.”
This morning (Japan time) I installed Security Update 2019-004 into my iMac’s High Sierra 10.3.6, but System Information still says the same thing about MRTConfigData.
I searched for files that has the text string “METConfigData” in the name, and EasyFind found two files named com.apple.pkg.MRTConfigData…, one ending with".plist", and another ending with “.bom”, and both are in /System/Library/Receipts, and are dated 2018/01/27, 15:59.
Howard Oakley’s page says High Sierra should have MRT Config Data version 1.47, 18 July 2019, but my iMac’s High Sierra system doesn’t have that! It says only version 1.28 of January 2018.
However, there is an application named “MRT” in /System/Library/CoreServices, and its last modified date is today, July 23, 2019, 9:50 AM (Japan time), that was when Security Update 2019-004 was being installed.
That would seem to indicate to me that you don’t have your System Preferences properly configured to receive updates. Go to System Preferences->App Store and make sure you have checked both the “Automatically check for updates” and “Install system data files and security updates” enabled. The security updates mentioned here are not the same as the update you manually installed today, rather they are critical background (silent) installs.
System Information only shows you the dates when a particular package is installed, so it will show you that Security Update 2019-004 was installed, but not the individual components like MRT.
Yes, you have been looking in the wrong place for your current version number. That app is what was installed with the Security Update, so you are now fully up-to-date. There is a Terminal command you can use to see what version you have, but a much easier way is to download Howard Oakley’s SilentKnight or LockRattler app from SilentKnight, silnite, LockRattler, SystHist & Scrub – The Eclectic Light Company and run it when you hear there has been an update.
Hi Al, thank you for your message.
That would seem to indicate to me that you don’t have your System Preferences properly configured to receive updates. Go to System Preferences->App Store and make sure you have checked both the “Automatically check for updates” and “Install system data files and security updates” enabled.
Yes. I’ve checked System Preferences’ App Store tab right now, and the settings are indeed set as you said.
Yes, you have been looking in the wrong place for your current version number. That app is what was installed with the Security Update, so you are now fully up-to-date.
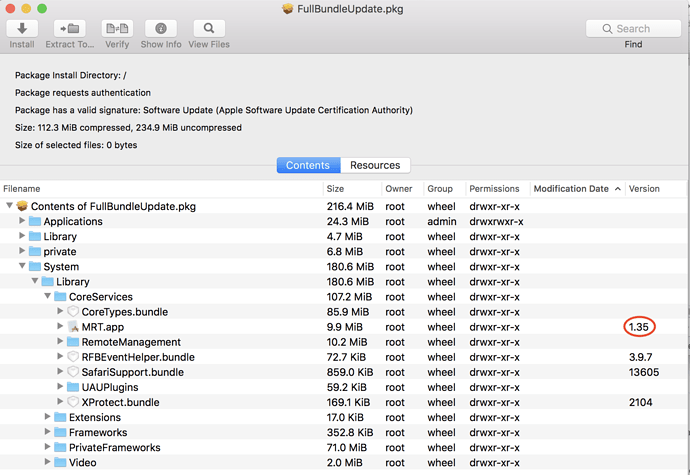
Finder says that the version number of the MRT application (currently in my //System/Library/CoreServices) is 1.35 (created on June 14, 2018, 9:02, and modified today, at 9:50.
Howard Oakley’s SilentKnight app (version 1.1 (2)) complains Gatekeeper is version 135 which should be 173, and MRT is version 1.35 which should be 1.47.
So, my question is: why did Apple fail to update those versions? Security Update 2019-004 certainly updated my system this morning (and did modify the MRT app), and why didn’t it make them “up to date”?
I was in Mojave, so had to reboot to High Sierra to figure out what was going on.
I am able to verify that the version of MRT that comes with Security Update 2019-004 for Sierra is 1.35, and since you had an older version before, it was updated. I have no idea why Apple chose not to include the latest versions. They have a special package included with each update designed to do exactly that. There are several projects that are managed by individual development teams that operate independently of the main macOS engineering team. Examples are Safari, iTunes, MRT, Gatekeeper, XProtect, etc. A separate package called “FullBundleUpdate.pkg” is part of each update with the intent of gathering those disparate items into the update. Again, I don’t know that this was an error or there was some underlying reason for using an older version. I can tell you that it’s not at all unusual as I see it with just about every update.
In my case, I already had version 1.47 and the installer was smart enough not to downgrade it, but I’ve seen that in the past, as well.
What should happen in your case is that within 24 hours, the system should check and bring any of those “system data files and security updates” up to date in the background, as long as your Mac is awake and you are logged in. But judging from what you’ve observed, that probably isn’t going to happen. There is almost certainly something systemically wrong with your setup, but I have no idea what it might be.
So you can either wait 24 hours while logged into your computer to see if the updates take place or if you don’t feel you can wait, use SilentKnight, since you already have it, and if it shows “updates available” for Gatekeeper and MRT, click the “Install all updates” button and be done with it…for now.
A post was split to a new topic: Recording audio from Zoom calls
This morning (Japan Time), after seeing Agen’s TidBITS Talk message, I let the App Stare app install a newly released
“Security Update 2019-004 High Sierra 10.13.6”, on my iMac running macOS High Sierra 10.13.6.
A week ago, I let it install “Security Update 2019-004”, which updated my iMac to High Sierra 10.13.6 (17G8029).
This morning, after the new update, my iMac says it’s running High Sierra 10.13.6 (17G8030).
Safari was not touched this morning - it had been updated to Safari 12.1.2 (13607.3.10) last week.
According to Howard Oakley’s SilentKnight, even after the new Security Update this morning,
Gatekeeper is still version 135 which should be 173, and MRT is still version 1.35 which should be 1.47.
So, it looks like Apple is still thinking version 1.35 of MRT/Gatekeeper is enough for macOS High Sierra 10.13.6.
P.S.: About an hour ago, I sent this message using a wrong method to Post. Sorry Adam, please disregard the message of mine an hour ago (7:55 AM Japan time), and use this message instead. Mark (Masatsugu) Nagata