Originally published at: Rapid Security Responses for iOS/iPadOS 16.5.1 (c) and macOS Ventura 13.4.1 (c) - TidBITS
Apple has re-released the recent Rapid Security Responses for its flagship operating systems to plug a WebKit vulnerability that’s being exploited without causing website loading issues. Install the updates as soon as feasible.
On iPhone 13 mini it took 3 min 20 sec
About same on MBP 16 inch 2021
Well, there now seems to be a (c) security response. Now sure what happened to (b), but (c) is downloading on my iPhone as we speak.
Might anyone installed " macOS Ventura 13.4.1 (c)" and come to realize that there are no issues with this version?
I am usually quite wary of installing system updates but not security updates, until I was away from my MBP for 24 hours and then saw that earlier versions of this security update had problems………
Thank you!
I cannot install it personally, but have heard from a few users and several ITs responsible for hundreds of Macs that they have not seen any issues yet.
I have it installed and see no issues, but I never had issues with the first installation on iPhone, iPad or Mac.
It installed for me and I haven’t seen any issues, but I didn’t have any issues with (a) either, so my experience might not be indicative…
So that’s 2 IIRC of I’m not sure how many RSRs that have had problems. (I don’t have it switched on).
Many of us here pause before installing updates, just to let things settle and not be on the bleeding edge of chaos. Tidbits editors often recommend exactly that.
The whole RSR thing needed to be bullet proof to build confidence… and it just isn’t. “It just (doesn’t) work(s)”, as it were.
I wonder what the actual split in Tidbits is of those that install everything immediately (or let it be installed by those things that autoupdate), and those that don’t?
Mark my words, this incessant push to get people to install each and every update ASAP is going to get even stronger with RSRs along the lines of “well you can always remove the RSR again if it gives you trouble”.
By now we’re essentially being coerced to weekly reboot our systems because of supposed “threats in the wild” and SSV and updates to the update, yada yada. It’s almost as if we’re celebrating that we’ve successfully traveled back to 1990 with its “have you tried rebooting it?” and selling this malarkey with “but hey it’s only 5 minutes instead of the 45 it took with Big Sur”. I’m not a fan at all.
No, there have been only two RSRs ever, and there were no problems with the first one.
It’s certainly a shame that on the second try, there were problems. It’s not clear to me that they were exactly Apple’s fault though—it sure looks like it was websites being sloppy in how they determined user agents and reacted to failures.
Seems to me that there are three possible ways forward:
-
People get suspicious about updates, don’t install regularly, and have only themselves to blame if their devices are compromised by malware bots. But Apple won’t be happy about this because of (a) legitimately wanting to protect users and (b) the bad PR that comes once Apple devices are being compromised more seriously.
-
People install the updates shortly after they’re made available and retain control over when that happens.
-
Apple eventually determines the risks are too great and too few people are installing the updates, so it moves toward a system that automatically updates without the user having a say in the matter.
I can’t speak to the sort of attacks that Apple is defending against from personal knowledge, but Lauri and I have spent non-trivial amounts of time over the past week fighting off literally hundreds of spam accounts created in our WordPress system by Russian spambots that are evading the protections in our Stop Spammers plugin and even sometimes the new email verification plugin I added to the account creation process. At least we got things set up properly with Stripe to prevent these spambot accounts from using our membership system to test stolen credit cards. Refunding a few hundred illicit charges was not fun.
It’s easy for users to think that there aren’t significant security risks out there because, for the most part, everything just works. But the reason it just works is that there is a HUGE amount of work being done to block an insane level of nonstop attacks. It’s easy to scale bot attacks, and the attackers don’t care if they have a very low success rate. All it takes is that one unpatched device and they can get a toehold that could turn into something big, like the LastPass breach, which involved two individuals being compromised, one after another.
The security update did not install on two MacMini‘s running Ventura 13.4.1. The (german) message was „could not personalise the update“. Several retries (also after reboots) have not changed the result. Any clue why this doesn‘t work?
P.S.: on my iPhone and iPad the update succeeded flawlessly
To me, not working with Facebook and Instagram would be a feature, not a bug. ![]()
No, I’ve not heard of anyone else having that issue. Do you have an unusual iCloud/Apple ID setup in some way?
Many thanks for looking into this, Adam! I am not sure whether my AppleID setup is very unusual: there are two regular users (i.e. without admin privileges), each with their individual AppleID. Then there is the admin user without an AppleID: for system administration tasks, one of the regular users enters the admin credentials. Both users make minimal use of iCloud: the only shared items are calendar, contacts, notes and books, and the “find my Mac”-service. For the security update, I provided the admin user with my AppleID, but only to get the same error message “update could not be personalised.”
I am travelling these days, but will be back home Friday to make another attempt. Cheers from Switzerland ![]()
Honestly, the only admin user not having an associated Apple ID does sound unusual because you’re combining higher permissions (admin access locally) with lower permissions (no automatic authentication to Apple). It should work, but it feels like an edge case that could run into trouble.
It is a sort of setup that I have been using since over twenty years - actually long before AppleID or iCloud existed. Just to be sure, I now have created a new AppleID for the admin and have tried the security update from that account, still to no avail. This is the error message (unfortunately in German):
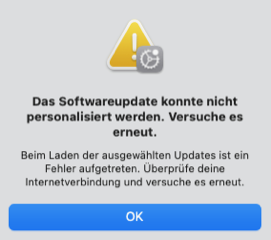
The translation: "The software update could not be personalized. Try again. An error occurred while loading the selected updates. Check your internet connection and try again.“
Hmm, I don’t know what to try next. May be a system recovery? Any other suggestion?
Many thanks!
Do you have an iPhone or other smartphone that can create a personal hotspot? What happens if you put the Mac on a completely different Internet connection?
If it were me, I’d just wait until the next full release of Ventura, but that’s partly because I don’t use Safari. If you can use another browser, you have essentially nothing to worry about.
Sounds like you haven’t tried to install the update in Safe Mode. That has been found to work for some users that have unexplained issues.
I will admit that I’ve never run across anybody that got that specific error message saying it “could not be personalized”.
Many thanks for your suggestions. I first tried to install in “Safe Mode”, but obtained the same weird error message. Then I followed your suggestion, Adam, and connected to my iPhone-hotspot: that did the trick! Congratulations!
Now I am at a complete loss what in my network configuration may have prevented the update: my macs are connected by LAN to a Fritz!Box 4040, which has an ADSL-line to my provider. Probably unusual in my setup: I also have a permanent VPN-tunnel to another, remote Fritz!Box. Adam, what made you think that it might be my network configuration, and any hints what might be wrong? All my other internet traffic seems to run fine…
In any case, many thanks for all your help, and for providing Tidbits to the community!
That VPN tunnel is where I’d look. There may be some combination of IP address masking or changes that Apple’s update server doesn’t like. (And I realize that’s a lot of hand waving. ![]() )
)