Originally published at: Juice Jacking Protection Setting Broken in iOS 26 - TidBITS
You may have heard about “juice jacking,” a type of attack that exploits a security vulnerability in USB charging. This vulnerability exists because USB ports can simultaneously transfer both power and data, potentially allowing a compromised charging station in an airport, hotel, or other public place to attack a connected iPhone.
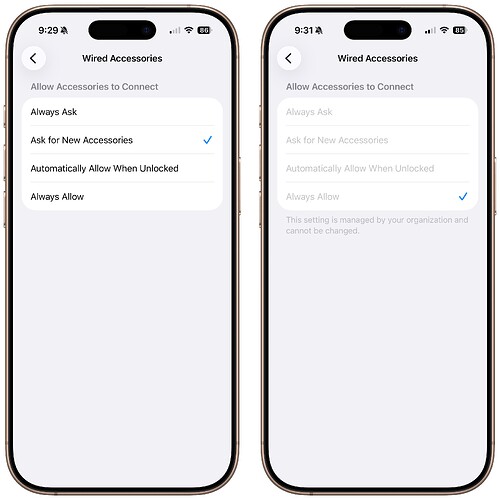
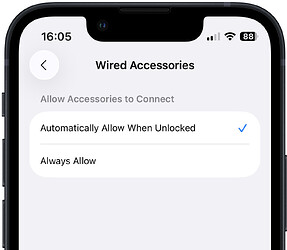
Although there are no reports of juice jacking attacks in the wild, Apple added protection against this vulnerability years ago with a setting that explicitly prompts you to allow wired accessories to connect. You can configure iOS to handle accessories in four ways: ask every time, ask only for new accessories, automatically allow connections when the device is unlocked, or always allow connections.
Protecting Against Wired Connection Attacks
Unfortunately, as a post on a private mailing list alerted me, there’s a bug in iOS 26.0.1 related to the accessory protection controls in Settings > Privacy & Security > Wired Accessories. The bug also affects iPadOS 26. For some iPhones and iPads, including both my iPhone 17 and fourth-generation iPad Air, the accessory connection control is locked to Always Allow, and a note below says, “This setting is managed by your organization and cannot be changed.”
However, I have no profiles or mobile device management (MDM) software in place—my iPhone and iPad are not managed by an organization. While I don’t recall which security level I had selected on my previous iPhone 16 Pro, I would usually have chosen Ask for New Accessories. Updating my iPhone 17 to iOS 26.1 beta 3 did not unlock the accessory protection controls. There was a suggestion that erasing all settings would allow editing of this option, but I wasn’t willing to try that. I’ve reported the bug to Apple.
While some people in the discussion also experienced the bug, others had no trouble adjusting their accessory protection controls. One person was confident that she had not previously chosen Automatically Allow When Unlocked on her previous iPhone, but she was able to switch back to Ask for New Accessories. Sadly, it is common for some settings to change during operating system upgrades.
Real-World Concerns?
Because this bug forces a reduced security stance, it’s worth examining the seriousness of the underlying juice jacking threat. Official warnings regarding the vulnerability appear regularly. They have come from the U.S. Army Cyber Command, the Denver office of the FBI, the Federal Communications Commission, the Transportation Security Administration, and the Los Angeles County District Attorney’s Office, among others.
But how can we reconcile all these warnings with the absence of reporting on real-world attacks? The first juice jacking exploit was demonstrated at the Defcon security conference in 2011, showing how attackers could take advantage of USB vulnerabilities to compromise a device. Researchers have since demonstrated additional attack techniques using malicious chargers. In 2013, Apple and Google introduced protections for iOS and Android, and both companies have continued to release updates and fixes for related vulnerabilities.
At one level, both Apple and Google are taking the threat seriously because the vulnerabilities are real, even if they originate only from security researchers demonstrating their findings at Defcon. That alone could help explain the persistence of the juice jacking warnings, especially in conjunction with the feedback loop between government agencies and media outlets.
However, I’ve seen a credible report of juice jacking being observed in the wild, an incident that may have helped prompt the additional protections we’ve seen in iOS and Android. It’s also possible that organizations like the U.S. Army Cyber Command possess knowledge of targeted attacks that haven’t been made public. Such attacks would have to be highly targeted because juice jacking requires risky physical access to the compromised charger.
Some experts suggest that juice jacking on its own isn’t a real threat, but it could be used alongside other exploits. This matters because sophisticated attackers—typically state-sponsored groups—collect various security vulnerabilities and strategically combine them to craft more effective attacks. They carefully select when and how to deploy these exploits, usually targeting specific individuals or organizations rather than the general public. This targeted approach explains why many attacks go unreported: if a vulnerability is exploited against a high-value target like a dissident or journalist, it will stay secret unless the victim notices the breach and works with security experts to find and report the flaw to the vendor for fixing. In short, even if juice jacking is unlikely to pose a threat to everyday users, it remains part of the broader security landscape that Apple needs to defend against.
Sensible Precautions
The practical takeaway here is not to worry much about juice jacking. Apple should fix this bug promptly to protect high-value targets, but no organization would risk exposing itself and neutering a valuable exploit by compromising many public chargers—especially in an airplane, say, in the hope that an undirected attack might find something valuable.
It’s also trivially easy to protect yourself if you have even the slightest concern. Use your own trusted charger and cable, or charge directly from a battery that you recharge using a public charger. Wireless charging is likely safer as well, since it has a smaller attack surface due to transmitting only power and minimal metadata (power negotiation and accessory identification from the phone to the charger). Although power-only USB cables are available, it’s hard to know how safe they are. It’s even possible to create exploit-enabled cables, so it’s best to stick with known cables from Apple and other reputable manufacturers.