Originally published at: iOS 14.4.1, iPadOS 14.4.1, macOS 11.2.3 Big Sur, and watchOS 7.3.2 Address WebKit Security Vulnerability - TidBITS
Apple has updated most of its major operating systems to address what would seem to be a severe WebKit vulnerability.
Another week and another 2.4 GB update requiring >30 min and a restart. This time to patch a vulnerability in WebKit.
I don’t know about the rest of you, but if this is the new normal, then SSV sure isn’t working for me.
I haven’t seen an explanation for why the updates for Big Sur have been so large. @mjtsai suggested perhaps it was related to the dyld_shared_cache, but that’s something I don’t understand, not being a programmer.
https://mjtsai.com/blog/2021/02/25/macos-11-2-2/
Weirdly, Apple said Big Sur was going to have faster updates, though not because the updates would be smaller.
As I wrote, it’s related to SSV specifically the fact that 4 GB worth of dyld cache now has to be provided freshly with every OS update courtesy of SSV.
Ach, right—I forgot that Howard had written about it already.
I do still wonder a bit, since his numbers add up to over 4.6 GB compressed, whereas the updates are in the 2+ GB range.
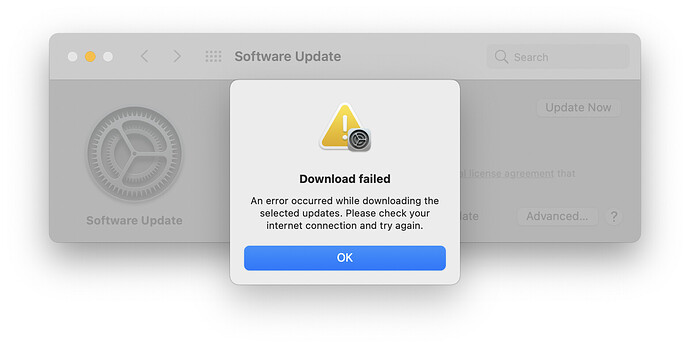
Have people been able to update to macOS 11.2.3? On both my 2020 iMac and my M1-based MacBook Air, I’m getting download failures every time I try. I’ve restarted, tried in different accounts, switch from Wi-Fi to Ethernet, and more, all to no effect. The Download Failed error occurs at wildly different points in the download too. Sometime it’s right away, once it was nearly done.
I’ve seen a few download failures in the past, but never this level.
It ran fine on my 2015 MBA yesterday late afternoon.
I upgraded my 2014 MacBook Pro to 11.2.3 without difficulty.
And of course, as soon as I complain, it works fine. Grumble…
Well, at least on the iMac. It still won’t download on the MacBook Air.
And Safari 14.0.3…on my Mojave MacMini (2012); Big Sur on an Early 2015 going ok with a 2.44GB 11.2.3 update.
(One thing I noticed is this is taking incredibly longer. Not just for the download, but there is the download, the “preparing”, the “verification” on iOS devices, then the Installation time. I came back to note this and my MBP is still in the “Preparing” phase.
The update didn’t fix the widespread Thunderbolt/USB speed issues that people are having when either attaching SSD’s directly to an M1 Mac or through a Thunderbolt 4 or Thunderbolt 3 dock. What a mess. My OWC TB4 dock get 150 MB/s vs my TB3 dock which get 600 MB/s with SansDisk SSDs that get 900 MB/s when attached directly to the M1. I’ve read some people with Samsung SSD’s have the opposite problem and experience degraded speed when attached directly to the M1.
Hey, how about a view for us old people with old computers — how far back in model history do these security issues apply? Neither my iMac nor my iPhone can be updated to current operating systems, and I know from my neighbors in our gray-haired neighborhood that I’m not alone.
Please consider that old people are very likely targets for security attacks, and when Apple comes out with a security update, they appear to have forgotten that a lot of us old people have been customers for a long while.
Nobody wants to landfill their old still reliable Apple hardware – but we need to know what’s insecure.
PS, as an example – so I look at Security and Privacy and find com.apple.WebKit.networking.xpc in the list at /Firewall/Advanced. OSX 10.13.6. Should I worry?
It would be a lot easier if you just told us what model’s you have, but an even easier solution is to check your System Preferences & Settings/General->Software Update to see if anything appears. If not, then your hardware is obviously too old.
I don’t understand what would cause you to ever worry about that specific entry.
mid-2010 iMac, OSX High Sierra. So, no security issues.
Thanks for your advice.
Since Apple isn’t providing security updates for High Sierra anymore, there’s no way to know from the presence or absence of an update if High Sierra suffers from the vulnerability. In theory, it should be possible to research the problem associated with CVE-2021-1844, but I can’t find more information about that quickly to determine if WebKit in earlier versions of macOS are vulnerable. Maybe @alvarnell knows more about how to research such things.
There’s a certain level of security through obscurity with obsolete operating systems. Since relatively few people have them, the attackers may be less likely to target them, even once they know that the vulnerability hasn’t been patched. But there’s no way to know for sure unless you update to a patched version of macOS.
I wish tech people would notice that older people not only have older hardware and software, but also have savings and are favorite targets of scammers. There’s an inverse “security through obscurity” situation here.
"… the act of scamming elderly people is a massive problem in the United States. Scams that start on the Internet are becoming more and more frequent among this population, too, especially as Internet-savvy folks start to age…
Yeah, yeah, if old people have enough money to be worth scamming, they have enough money to buy new computers. But often they don’t upgrade hardware.
I just went through this with an elderly neighbor and with the ISP we both use, which claims gigabit speeds but can only deliver a third of that to someone using a 2010 Mac. “Your computer is too old” is the problem.
I don’t see this situation getting better with time.
In a perfect world one could go to CVE - CVE-2021-1844 and it would say how far back this WebKit vulnerability was applicable, but as you can see no-one has yet gone back to give any details at all. It didn’t use to be this bad, but I do find it more and more these days. And Apple isn’t much better. The only way to find out if the vulnerability exists in a legacy macOS such as High Sierra would be for someone to develop a means running a test to see if it can actually be exploited, something I don’t have the time, skills or patience to accomplish.