I have two G-Drive 6TB Hard Disks that I have been using for backup. I am moving to all SSD drives and will donate these drives - and want to make sure all the data is unreadable. In the past I have done a secure erase - but that takes a long time for these large hard disk drives. So, this time I figured I would encrypt the drives, then erase and reformat - nothing would be readable after that. But, the encryption process has been running for 18 hours and it doesn’t look like much has actually been encrypted. (I am running MacOS 15.2 on a Mac Studio.) So, it looks like this process is even slower than a secure erase. Has anyone had experience with encrypting these large hard disks? (There is 5 TB of data on the 6TB drive.) I am wondering if I should just stop the encryption and revert to the secure erase.
When I have run a Finder Encrypt command, I remember it taking a day or so. I think it was on a 8 Tb drive. Not sure if having the Finder in the forefront makes it happen faster.
If the purpose is to wipe the drive for resale/donation, the encrypt method is time consuming overkill. Changing/losing the enrcryption key is a fast easy method if the data has been encrypted all along. But if that’s not the case, I wouldn’t do it that way.
If your drive (and its enclosure, if it’s external) supports a secure-erase mechanism (e.g. the SATA 3 “SANITIZE” command or the older ATA “Security Erase” command, the SCSI/UAS “FORMAT UNIT” command or PCIe/NVMe’s “FORMAT NVM” command). This should tell the the drive hardware to securely erase everything using a mechanism the manufacturer considers appropriate, including normally-inaccessible regions like the pool of blocks marked as bad or spare. I know of free software for Windows and Linux that can issue these commands but I don’t know of a Mac utility for this.
If you can’t issue a secure-erase command directly to the drive, then my recommendation is to perform a fairly generic one-pass erase command (write zeros to every block). For example, one of the following commands (after unmounting every volume on the disk):
$ diskutil zeroDisk /dev/disk###
$ disktuil randomDisk /dev/disk###
Where disk### is the media’s device name (e.g. /dev/disk5). Make sure you don’t provide the wrong device name, or you’ll end up wiping stuff you want to keep and will have to recover by restoring from a backup and/or reinstalling macOS.
You could also use the diskutil secureErase command and select one of the multi-pass algorithms, but I think that is unnecessary overkill. The goal of those is to try and scramble the magnetic signature to eliminate any hints about what might have previously been recorded. But I’ve never read any paper showing actual data recovery from this, only theoretical papers describing how it might be possible. And those are all from the days of MFM/RLL hard drives, where software could access the raw magnetic bit-patterns. With modern hard drives, even the authors of those original papers say it’s not possible.
Ditto for those who talk about data recovery using a magnetic force microscope. Although researchers have seen magnetic after-images on erased media, I have never seen a single document describing actually recovering files from those after-images.
In other words, if your data is so sensitive that you think you can’t trust a simple one-pass wipe with zeros or random values, then you shouldn’t trust anything and should physically destroy the device.
I also remember that I could not figure out a way to get it to stop encrypting once I started it. Will those command lines stop it if it is already encrypting?
I’m not sure. It was my experience that the FileVault software can’t change the status of a drive while encryption/decryption is in progress.
When, several years ago, I tried to use it to encrypt a laptop drive and found that it wouldn’t complete after several days, I couldn’t stop it. I ended up wiping the computer and restoring from a backup in order to make it stop.
Now in the case of an external drive, you might have better luck. If you unmount its volumes and then wipe the drive (not its volumes), that should clobber the partition table and all of the per-volume file system structures. Hopefully that should wipe whatever macOS uses to record the encryption state as well.
The first drive completed this morning - about 40 hours in total I think. The second drive is still running.
These drives were not encrypted originally - if they had, it would be easy to erase and throw away the key. But I don’t encrypt my external backup drives because they don’t leave home and are stored in a locked fire safe. (I understand “best practice” is to store of-site copies, but I never thought that was necessary.)
Thanks for the comments.
David
If anyone is able to read them, it will be government organisations. If they are interested with what is on your disks then you will have much greater problems, and they have a lot easier ways to find out.
Found this old thread because I started doing a Finder encrypt of an external 2TB HDD on Friday afternoon 48 hrs ago. It is formatted APFS so has built in encryption but the instant on and off only applies to the internal drives, it does apply to externals.
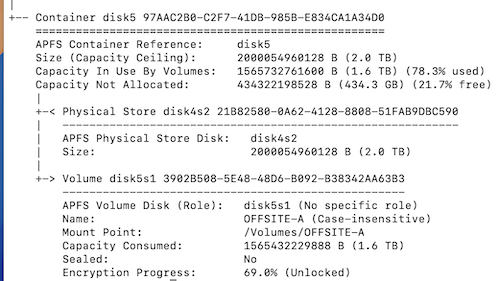
The actual time depends on a lot of factors, but I learned that you can monitor progress by entering diskutil apfs list in Terminal:
So my 2TB HDD connected to an M1 MBA will take three days.
It is faster if you turn off I/O throttling: sudo sysctl debug.lowpri_throttle_enabled=0
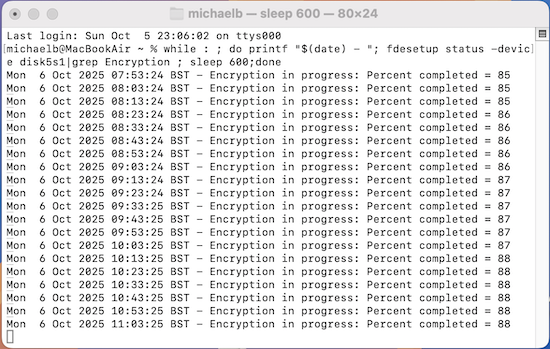
You can monitor progress with while : ; do printf "$(date) - "; fdesetup status -device disk5s1|grep Encryption ; sleep 600;done
Yes. The automatic hardware encryption feature of Apple Silicon (and the T2 chip in Intel Macs) only works on the built-in SSD. External drives are encrypted/decrypted in the traditional way, which unfortunately, can take a long time.
This is (I assume) because internal drives are always encrypted. When you enable File Vault, it wraps the drive’s key with another layer of encryption, unlockable with a valid user’s login (or the recovery key).
But you probably don’t want this with an external drive - the expectation is that you will move the drive to other computers, which may not support File Vault (e.g. Windows and Linux PCs). So when the drive is not encrypted, it must be actually unencrypted.
Thanks for these tips. I don’t do this very often but have filed away for next time.
Your monitoring progress method is much better then diskutil apfs list because it updates itself if left running:
However turning off I/O throttling seems to have slowed it down. The first 75% took 55hrs (1.36%/hr) and the 13% since I turned off I/O throttling have taken 12hrs (1.08%/hr). Maybe it isn’t a linear process and it gets slower as it approaches 100%? I have re-enabled I/O throttling to see what happens.
That’s because the command is a while loop. It repeatedly calls fdesetup status until you stop it.
I also noticed the following on the fdesetup manual page (type man fdesetup):
So I wonder if you might be able to skip the while loop and just type
fdesetup status -extended -device disk5s1
or maybe even just:
fdesetup status -extended
Thanks for useful inputs in this thread.
Just to close this out now that the encryption is complete:
- 0-75% took 55hrs, I/O throttling on: 1.36%/hr.
- 75-88% took 12hrs, I/O throttling off: 1.08%/hr
- 88-100% took 10hrs, I/O throttling on: 1.2%/hr
Total time 77 hrs, avg rate 1.3%/hr. It doesn’t seem to make much sense that turning off I/O throttling should slightly reduce speed but maybe there is some deep explanation.