Originally published at: Beware Obituary Scam Sites and Fake iPhone Security Warnings - TidBITS
A longtime TidBITS reader contacted me in a slight panic yesterday. While searching on his iPhone for an obituary, he tapped a possible result in the Google search results. The site to which he was sent threw up a bunch of dire-sounding warnings about how his iPhone was infected
He freaked out slightly but rightly immediately closed Safari and hoped all was well. However, 10 minutes later, he received an email from 1Password informing him of a sign-in from a new device or browser extension. That threw him for a loop, so he contacted 1Password support, who confirmed it was a legitimate, coincidental message—seemingly fully unrelated to the malicious site visit.
I want to share how I helped reassure him that there was no reason to worry so you can repeat the process if you or someone you know experiences a similar Web-based malware lure.
Examining the 1Password Notification
I was first curious about the IP address that 1Password identified. When I asked my friend to check it using What’s My IP, he confirmed that it was indeed his IP address as the source of his new sign-in. That confirmed it was at least one of his devices on his network, not a malicious party elsewhere on the Internet.
While it’s not inconceivable that malware could have compromised his device and signed into 1Password from it, it’s quite unlikely due to an extra step 1Password requires: you need both your account password and a Secret Key to log in. (The Secret Key is essentially a second randomly generated password that’s combined with the account password to create the encryption key that protects your data. It’s only stored locally on your devices.) It’s vanishingly unlikely that malware could somehow have exfiltrated the Secret Key from local storage, decrypted it, and combined it with the account password to log in. Nothing is impossible, but malware with such a capability would be used against high-value targets by criminals or governments, not against random people browsing the Web.
I can’t explain why my friend received this notification despite not signing in to 1Password manually on his iPhone or Mac. Research suggests that the message can be triggered by force-quitting Safari, using iCloud Private Relay, clearing the browser’s cache or history, updating the 1Password extension, having a dynamic IP address change (which causes 1Password to think it’s running on a new device or location), or updating 1Password or Safari. Unexplained 1Password notifications seem to be uncommon, so it’s not that these activities will trigger a sign-in notification, just that they might.
Investigating the Malicious Website
Based on years of reading about iPhone security, I’m confident that iOS is hardened against attacks from random websites. In part, this is because Apple’s hardening efforts have been so successful that any ethically challenged person who discovered such an exploit would sell it for millions or use it for targeted attacks against high-profile cryptocurrency holders, as one example. Normal people would report it to Apple.
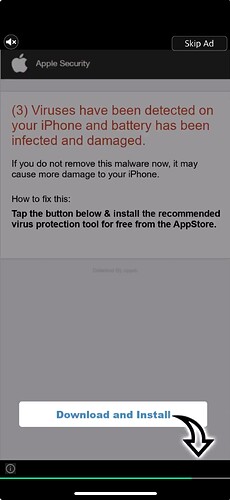
So I repeated my friend’s Google search and found the site he had clicked as well as several others, all with article post dates of 13 November 2024. The offending site was sloppily built in WordPress and contains what seem to be AI-generated obituaries. You can tell from sentences like “His sudden passing on [insert date] has left those who knew him grappling with loss.” Other signs include the sketchy gambling ads on the pages and the fact that the name of the deceased changes between the title and the text. Oops.
When loaded, the sites quickly started displaying dire-sounding alerts that claimed my iPhone had been compromised—and suggested a system cleaner app or VPN.
Tapping any of the links loaded a second page that immediately redirected to a system cleaner or VPN app in the App Store. I don’t know if these apps are legitimate, though I have my suspicions. I may be willing to navigate to malicious sites in Safari, but I’m not so foolhardy as to install potentially malicious apps on a non-test device.
I won’t link to these apps, but I have reported them to Apple for investigation.
Lessons
What should we take away from this experience?
- Coincidences happen: My friend was worried because of the 1Password notification, but as far as I can tell, it was merely a coincidence. Just because two events occur close to one another doesn’t mean they’re necessarily related.
- Don’t panic: The Hitchhiker’s Guide to the Galaxy had it right: Just because a website displays an alarming alert doesn’t mean that anything bad has happened. The scammers are trying to bypass your rational mind by invoking fear and danger.
- Close the tab or window: To make the scam website go away, tap Safari’s tab button in the lower-right corner of an iPhone or iPad and close the offending tab. On a Mac, close the window with Command-W. If you can’t get the tab button to appear on an iPhone or iPad, tap near the very top of the page—this often reveals the Safari framing.
- Don’t install random apps: If a website you didn’t intentionally visit suggests that you install an app and then redirects you to the App Store, don’t do it. Although Apple reviews all apps in the App Store, its vetting process is far from foolproof. Examples exist of legitimate apps being erroneously rejected while dubious ones slip through. You should always assess app trustworthiness based on factors beyond its inclusion in the App Store.
- Obituaries are easily faked: Perhaps the most troubling aspect of this scam is how it preys on people who are grieving, particularly the elderly. Since obituaries are often relatively similar, they’re easy to fake, and it wouldn’t be difficult to create a site that would automatically generate obituaries for every imaginable name. (Similarly offensive are sites that leverage obituaries to generate search traffic and thus ad impressions with poor AI-generated obituaries, including of living people.)
Stay alert out there.