Originally published at: https://tidbits.com/2018/07/16/beware-new-bitcoin-extortion-scam-that-uses-stolen-passwords/
A new email scam claims to have images of you viewing pornography, and to make it convincing, it includes an old leaked password in the message. Don’t be fooled.
I just received one in my SPAM filter as I’m reading this article. What will they think of next?
Thanks to 1Password I wouldn’t even recognize a password I use at any web site.
“For now, if you receive one of these messages, just ignore it, and make sure to use a strong, unique password for each of your online accounts, which is easy if you use a password manager like 1Password or LastPass.”
There is one caveat to that, Josh, it should end like this: "…or LastPass, IF the website accepts the form of the generated password."
To many websites so severely restrict what form of an acceptable password, that 1Pwd/LP generated passwords are considered unacceptable. Here is an example from a U.S. Government site:
The PASSWORD MUST:
be 9 to 30 characters in length
contain at least one uppercase letter (A-Z)
contain at least one lowercase letter (a-z)
contain at least one number (0-9)
contain at least one of the following special characters: # @ $ % ^ ! * + = _
change at least four characters from your previous password
The PASSWORD CANNOT:
contain spaces
be one of your last five previous passwords
The PASSWORD will expire in 150 days.
It is only hit or miss if a random 1Pwd-generated password meets those requirements.
Here is an example from a U.S. Government site
The operator of that site should be asked to review “NIST Special Publication 800-63-3 Digital Identity Guidelines”
https://doi.org/10.6028/NIST.SP.800-63-3
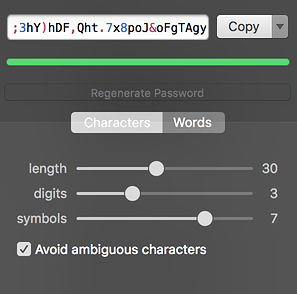
If you set up 1Password’s password generator to, say, generate a 30-character password with 3 digits and 7 symbols, you are almost certain to generate an acceptable password on the first try.
–Ron
What? You expect one U.S. Government agency to change because another U.S. Government agency did?! 
BTW, the overall owner of the site in my example is the Department of Defense!
Thank you for the suggestion, I’ll look into it at my next mandatory change.
Hope springs eternal, I guess.
The DoD is currently getting a certain amount of flak from Congress about their failure to follow NIST guidelines when it comes to infosec issues. Apparently, NIST reports have some actual statutory or regulatory weight with other departments beyond just being suggestions. If you complain, there is a chance that memoranda will be issued. Who knows, perhaps a task force or subcommittee will be formed. If you’re really lucky, a report might get issued. Progress!
At the state government level, I have worked with web site maintainers who basically said that they had thrown in the kitchen sink on password requirements in order to deflect criticism should they get breached. They were actually grateful to have official guidelines to follow so instead of “I just made it as complicated as I possibly could” they can say “I followed best practices as put forth by the National Institutes of Science and Technology.” As these decisions are often made my individual developers operating in a relative vacuum (yes, even at DoD), it can be surprising how much difference it can make.
–Ron
Those rules are very similar to the ones for Citizens One, the bank that administers the iPhone Upgrade Program. Super annoying.
Sophos has published an interesting analysis of this scam.
Sadly, this is old news. Here’s an article by Brian Krebs from 2018 describing the same scam.
And, for what it’s worth, I found one of these in my spam folder a few weeks ago. They password they showed me as “proof” is one they got from the 2012 LinkedIn data breach and which I changed at the time, since LinkedIn forced everybody to change passwords at the time.
Yep, my post was merely adding to our coverage from 2018. I was reminded of it in part by a friend who had just received one of these spams was tremendously amused — he couldn’t get his camera working on a Zoom call and was thinking of contacting the spammers to see how they’d gotten it to record his secret activities.