Ah, if only that were so! Imagine how much better macOS would be just by fixing things pointed out on TidBITS Talk threads! ![]()
That has not been my experience. My fstab file has remained intact and in the correct location through many updates from Sierra to High Sierra to Mojave and then a big jump to Sequoia.
No backup is created? I’ve found that whenever there’s a macOS update that trashes my customizations (for the Apache web server and SSH), the installer creates a /Users/Shared/Relocated Items folder (and an alias to it on my desktop) which contains backed-up copies of the replaced files.
Or, if the installer doesn’t overwrite the file, it will often place the factory-default version of the file in that location.
Either way, I can compare the relocated files against the active copies and put back any changes that the installer eliminated.
Only with the default configuration. If the EDITOR environment variable is set, vifs will launch the editor to which it refers. On my system, this is Emacs.
I use vi, but I know there is a more user-friendly editor that you can use in the terminal. So I asked an AI what it is called.
The more user-friendly terminal-based text editor you’re likely thinking of is nano.
Nano:
Simple and intuitive: Nano has on-screen shortcuts listed at the bottom of the terminal, making it easier for beginners.
No modes: Unlike vi/vim, you can start typing immediately without switching between command and insert modes.
Basic but sufficient: It supports syntax highlighting, search/replace, and other essential features.
It isn’t that I thought Apple had fixed; I thought Apple Intelligence had fixed it. And since I have Apple Intelligence turned off, that would be really scary. (Again, facetiousness.)
You attached the drive before you unlocked the screen or logged in? It may explain while the disk didn’t mount nor prompt for the password. If you save the password in the Keychain it will stop asking you for it.
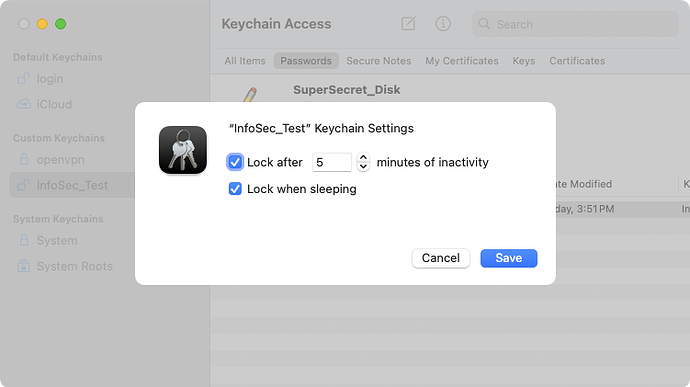
For higher security, I’ll have an encrypted DMG disk image or physical SSD/HDD and the password is saved in an additional keychain that locks after a period of time like 5min. To access these highly sensitive disks virtual or otherwise:
You need to unlock the extra keychain. It is not the login keychain but one for this dedicated purpose.
I know Keychain is being depreciated in favor of Passwords and if they do eventually kill it. I hope they replace it with something or add the certificates and other functions into the Passwords app. I bet they will keep Keychain but only the command line version. The ‘security’ command line tools manpage is extensive. Looks like it can do it all and then some. I’ve lightly used it to script certificate injections, etc.
After I’m logged in (or, more accurately, unlocked the screen). I eject and unplug the drive before letting the screen lock (or log out).
I have not saved the password in Keychain (obviously) and would prefer to be prompted. But I would like to type an answer to the prompt without needing to click.
Clever. I’ll think about that.
All the discussion here has been with UUIDs. You can use volume names - which is much easier. My fstab has lines like:
LABEL=CCC-Photos none apfs rw,noauto
If a volume name has spaces, need to use \040 in place of the space.