Originally published at: Never Change Your Password - TidBITS
Many websites advise you to change your password routinely. That advice is nearly universally wrong: you should only update a password when there’s a weakness. Why does it persist?
Excellent article. Thank you, @glennf.
I feel it wouldn’t be quite complete without this snarky reminder about how we should set passwords (of course right before we put them into a PW manager and forget about them forever).
But also!
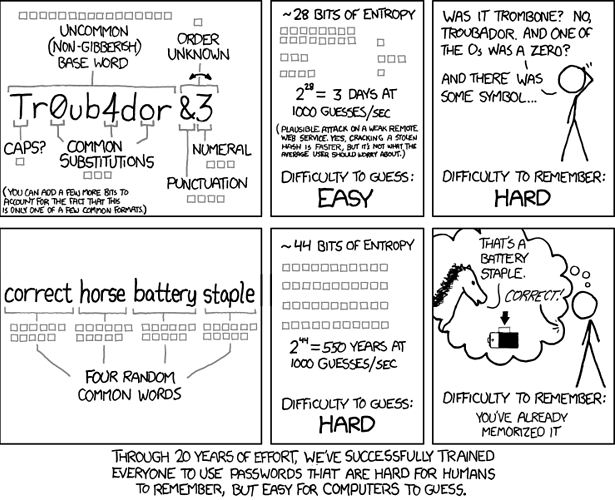
Because people re idiots…and for years have followed the advice by the DoD people…but even they have come around to the make it long but able to be remembered and don’t change it unnecessarily point of view.
I think the logic behind regular password changes is that data breaches happen all the time and you probably won’t find out about it until after you’ve been victimized.
So if you change your password every month, then in the worst case, the thieves have a password that will expire in a month.
Of course, this is complete BS. When a password is stolen, you can expect an attack within seconds. No thief is going to hold on to it for weeks or months before trying to use it, because they know it will be changed as soon as the data breach is made public, if not sooner.
And requirements for frequent password changes often causes people to make trivial changes each time. So “foo1” becomes “foo2” and then “foo3”, etc. If one gets stolen, it will be pretty easy to try out the next dozen combinations.
For a single password, absolutely: when phished or sniffed or socially engineered, the attacker knows they have a very limited window to attack.
My expectation is that for breaches at sites with lax security, as long as they’re encrypted, it can still take some time to start matching passwords via brute force—weeks or even months, if the breach isn’t discovered. Really, short and unsalted passwords are the biggest culprit. If a site requires, say, 12 characters and salts everything, only a targeted attack against specific accounts would probably result in any effective password recovery.
I would be more charitable and say that because most people aren’t security experts, they will follow what seems to be the best advice. So it’s contingent on people like us to spread the word to people who may refuse to believe it because they’ve been trained wrong for so long.
Though, honestly, a 16-character randomly generated password that you never type in is just great. If we retrained people to use the longest allowed password and a password manager, they can just forget all the other advice (except about not sharing passwords).
(Astonishingly, Microsoft still recommends a minimum password length of 8 characters in its Windows 10 administrator guidance and allows none longer than 14.)
In case others misinterpret this as I initially did, a user can choose a password longer than 14 characters. A Windows 10 administrator cannot set a policy that requires users to choose passwords longer than 14 characters.
Windows also still has a policy option that requires passwords be “complex” meaning it includes at least three different kinds of characters; lowercase, uppercase, numbers, non-alphanumeric keyboard characters, other Unicode characters. Your password can’t be eight poop emojis, but it could be six plus 1!.
This just posted. The timing with my article cracks me up.
Unmissable piece of comedy:
https://www.icloud.com/iclouddrive/0SIuzhx6ldThpftzyrRQDEuyQ#Passwords
–e.
No need for charity. DoD organizations consistently undermine security by their misguided policies of forcing password changes at the most, every six months. This does nothing but add to the burden of users seeking benefits info/support or health care support, if not actively p***ing people off to use deliberately weaker passwords. Glenn’s article is excellent and spot on, and I wish government IT folks would wise up.

I wish that it was a universal option, that merchant websites all have Guest Checkout. No need to create an account unless it benefits you(perks, discounts, member bonuses…). That would be less pwds to worry about and less breach concerns.
I agree, no need to change password unless breached and never use same one twice.
I should stress that there are a ton of sites that have limits on characters and length.
There have been many times where I was ready to purchase an item but they required I create an account with password. No thanks – I have too many already. Guest checkout is very useful.
Charitable to users.
I used to be more charitable about it…but best password practices are all over the internet from smart, knowledgeable people and they just get ignored. Corporate It departments who one would imagine are run by competent people are as wrong as often as non geek users…and that’s just deliberate stupidity on their part because they do…or at least should…know better.
This is all great advice. The NCSC has a good password guide aimed at businesses that specifically advises against practices like expiring passwords, limiting length, or imposing ‘complexity’ requirements. They also have a good infographic that can be passed on to unenlightened IT departments. 
The worst nuisance in the passwords area is when websites have a length limit, don’t bother telling you about it, and then silently truncate the password you create. Since you have no way of knowing that they’ve chopped off part of what you typed, you don’t know your own password. This has happened to me a few times over the years.
By the way, I don’t agree that everybody should use a passwords manager. There are alternative ways of saving passwords that are just as secure, if not more so, and I don’t like putting all my eggs in one basket. I’ve never used a passwords manager, but I assume that if your master password is lost or compromised, all your logins are now lost or compromised. (Please correct me if I’m wrong.)