Installed from a browser without interaction? As far as I know, all modern web browsers have features to prevent something like this.
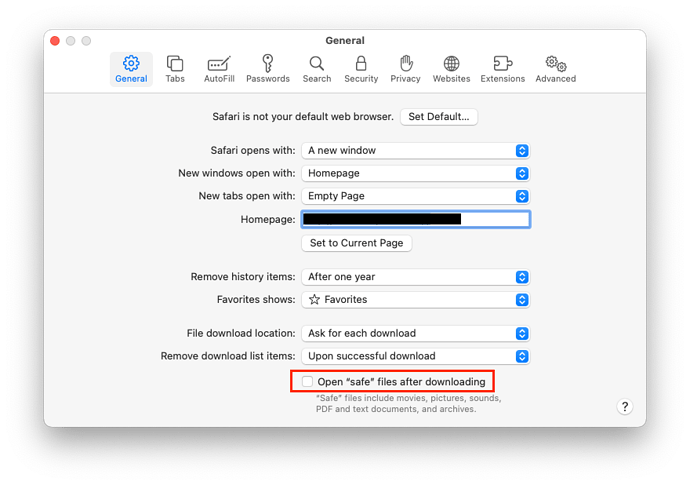
You should always configure your web browser to never auto-launch downloaded content. For Safari, be sure to uncheck the “Open safe files after downloading” box on the General tab of the preferences:
Other web browsers may have other settings to control this.
Assuming your web browser allowed something to auto-execute (e.g. an installer of some kind), there is also the system permissions feature that will prevent a non-administrator from copying any content to the /Applications folder without getting you to provide an admin user name and password. Without that, it could still install something to your home directory, but that can limit the damage to your login, and probably protect the rest of the system.
Finally, there is Gatekeeper, which forces you to authorize any downloaded application the first time you launch it. If you’re not logged in as an administrator, you will need to provide an admin user name and password in order to do this. If the app is not digitally signed, Gatekeeper will refuse to let you launch it at all (although you can manually right-click on the app and select “Open” from there to authorize an unsigned app.)
So, there are several layers of protection that are designed to prevent software from auto-installing without your knowledge.
But all systems have bugs, so it would be foolhardy to claim that such a thing is impossible. Apple and other reputable software vendors will fix these bugs as they are discovered (which is why it is important to keep apps up to date), but sometimes they are exploited before they can be fixed (so-called “zero-day” exploits).
WRT anti-malware software, I have an installation of the free edition of Malwarebytes. I run a manual scan from time to time, when I think it’s been a while. So far, it hasn’t found anything, but I am very careful about what I download and where I download it from. I have never run a background-scanning app on my Macs. (I run Microsoft Defender on my Windows PCs, and don’t bother to run anything on my Linux systems, but that’s a different topic.)