…and that, in my opinion, is exactly the problem with Apple’s attempt to make it “simple” and “elegant.” (The same general issue applies with Messages contacts that have multiple paths to send Messages, e.g., phone numbers, iCloud email addresses, etc.)
I started setting my mail clients to NOT automatically load remote content (mostly, that’ll be images, but could be almost any kind of attachment as well, usually with tracking attached) looong ago to avoid delays between loading embedded (e.g., images actually in the email message) vs. remote content – as I viewed messages.
These days, your Mail client will automatically pre-fetch the remote content for each message “when received”. So that when you view the message, you’ll see both the embedded and remote content together without the delay for fetching remote content.
[The URL used to fetch each item of remote content is commonly quite long and contains some seemingly random alphanumeric characters. Mostly for tracking, to identify the specific message and recipient the content is being fetched for. The server providing the remote content receives that, along with the date & time of the fetch, and the IP address of the fetching program. The fetched content itself can contain all sorts of things, even including scripts for your Mail client to run.]
To make this NOT happen automatically in Mail turn on “Block All Remote Content”. Then it’ll only happen when you click on that “Load All Images” at the top of the viewed message. You may find that most email messages are readable and usable without their remote content.
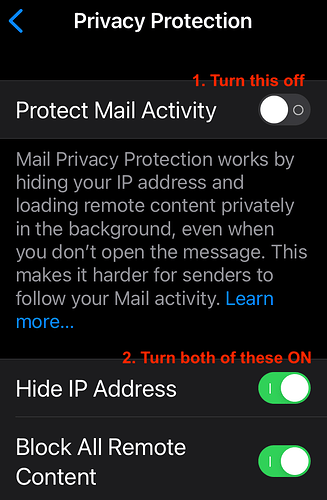
For anyone as confused as I was, turn off Protect Mail Activity to see the other two options.
However, after turning on both options (Hide IP Address and Block All Remote Content) and then turning Protect Mail Privacy back on, I turned Protect Mail Privacy off again and found that Block All Remote Content had been turned off. @bob32, I take this to mean that you recommend that I leave Protect Mail Privacy off after turning on both options. Do I understand that correctly?
In my case, with protect mail activity on, they merely get the IP address of the Apple server that fetched the content.
As I said, I’ve tried it, and it doesn’t work well for me. This starts happening (remote content disappearing) for me when there are issues with iCloud private relay.
Indeed. That’s the only way to turn on Block Remote Content (at least). Seems counter-intuitive, to me.
I don’t seem to see that problem. Running iCloud Private Relay with Maintain General Location.
The problem with private relay is that you are still downloading the content. So the operator of the server (a potential scammer) may not know your IP address, but they will still know that you downloaded the image.
It is a common practice to include personalized information (e.g. sequence numbers) in the URLs to the downloaded content. So a scammer can know that you opened the mail, even if the image is downloaded via an Apple proxy server.
If you block downloading of all remote content, then they can’t get that information unless you explicitly request it.
As I said, I don’t open sketchy emails. My biggest issue is with iPad Mail, which will open another message if you delete one that you are reading, but I solve that by opening another message and then deleting (or archiving) the one I just read. For Mac mail, I have preview turned off. iOS obviously doesn’t have preview, so I don’t worry about it there.
Sketchy emails, if they make it to my in box, get moved to my TrainSpam folder for that account and hopefully spamsieve will take care of them going forward.
So, for me, turning off images is just annoying for most message that contain them.
I’ll add that what would be a nice feature for this would be a control when you load images to “always load images from this sender”. On Mac I know that there are mail apps that have this feature - Thunderbird, Postbox IIRC.
Another annoyance with Mac Mail is when viewing the full headers of a message. For some reason, the Message-ID label is not included, making it harder than it should be to figure out which text string is the actual message ID.
The Message-ID label is included if you view the source (View → Message → Raw Source). Because of this and other inconsistencies in how macOS Mail handles “full headers”, I usually just go directly to the source.
Thanks, that’s good to know!
Another annoyance with macOS Mail is that find does not extend to email headers. Not even if you first click in that space. I actually have to bring up the full source just to be able to use find on it to see, for example, if a certain name was included on a very long list of addressees. Does not exactly help staying on top of email and potential fraudulent use.
Just for clarity, here is a screenshot of the relevant settings for iOS Mail Privacy discussed above. Apple’s interface is not exactly intuitive for this process. Turning the top setting on does NOT block remote content. You can see this by turning both lower settings on, then turning the top setting on and back off again. You will then see “Block All Remote Content” has been switched off.
Settings > Mail > Privacy Protection:
[Edited to add location]
Useful tip - thank you.
The iOS UI doesn’t help when this setting is hard to find. I typed “privacy” in the iOS Settings search window and there was nothing listed for Mail. The setting “Privacy Protection” is part of Mail settings (in the Messages section)…
So it seems there are three options:
-
Select “Protect Mail Activity” which hides my IP address when an email “calls home” to obtain remote content and loads that content “privately”. That content could be nefarious. In any case the Apple explanation that remote content is sought “even when you don’t open the message” concerns me. I tend to swipe and delete unwanted emails before opening them. I don’t want the sender to know it has been received, even though the IP address will be blocked (bearing in mind Shamino’s comment about the remote request possibly identifying me in other ways)…
-
Deselect “Protect Mail Activity” and manually select “Hide IP Address” (essential) and “Block All Remote Content” - some users prefer this for extra security
-
Just select “Hide IP Address” and don’t block remote content - risky!
Protect Mail Activity causes the system to auto-load remote content using an Apple server. So any scammer won’t know where you are (since the requests will all come from an Apple data center), and he won’t know if/when you read the message.
But you’re right, he could infer that the e-mail address is valid, since something is downloading the content. On the other hand, he could also infer that from the fact that the mail didn’t bounce.
Hide IP address uses (I think) a proxy server when fetching remote content, so the sender won’t know the address of your phone/computer. I’m not sure why this exists separately from *Protect Mail Activity".
Block All Remote Content means you only see what is actually attached to the mail. If any content needs to be fetched from a server, it won’t be done until you tap the link telling it to actually fetch it.
I see no reason why you couldn’t use all three at once. Don’t download content until you request it, and when you do, request it via Apple’s servers.
For myself, I just block remote content. If it’s mail from someone/something I know (friends, relatives, newsletters that I’ve subscribed to, etc.), I’m not concerned about the sender knowing if/when I’ve downloaded remote content. And I don’t download content from sources that look spammy.
I’m far less concerned with my IP address being known. Every time I visit a web page, the remote server gets my address. If I was seriously concerned about that, I’d get a VPN and do all of my networking through it. But I’m not, and I don’t.
I concur. Nor is the Apple description very clear as to what is happening, unfortunately.
My personal speculation, based on observed patterns and decisions by Apple in their systems, is that often things are driven by their mandate to get everyone using their cloud services in any way possible while still somewhat retaining a very limited “choice”.
To be fair, the Mail Privacy Protection settings may simply be an example of bad UI design and/or description text. However, I have noticed a growing number of seemingly forced directives in how settings are designed or described that strongly imply a pattern of “get them on our cloud services.”
Sigh, feels like my permanent state lately (don’t tell anyone or they’ll come looking for me)
And paranoid, did I mention paranoid… ;-)
Just because I’m paranoid doesn’t mean they aren’t out to get me.