Thanks! I think that’s my first appearance on Schneier’s site.
Spam filtering effectiveness varies greatly among email service providers, which is one reason I have been using Runbox.com for years now. . . The Norwegian employee-owned company focuses on user privacy and security. And when it comes to spam, their filtering is very effective. Hardly any spam makes it past Runbox and I cannot recall the last time I got a phishing message. Runbox customer support is also among the very best I’ve experienced.
One of my favorites was similar to the first scheme you described, telling me that a certain email’s password was going to “expire” in a few days. It came from “Web-Mail Support”
“Hello ,
The password for web@blahblahblah.com expires in a few days. You can change your password or continue to use the same password.”
This was followed by a button labeled “Keep the same password”.
Since I am, in fact, the email support for our very small non-profit, and set up all the accounts and passwords, I just blocked them and ignored it.
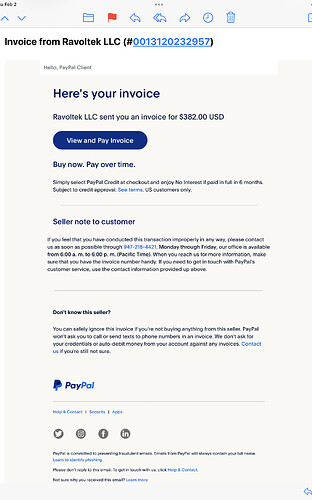
Anything that takes me a few minutes to decide if it is spam is dangerous. For people in a hurry, worse. This came today, complete with the footer about “Learn to identify Phishing”. I ended up looking up the LLC “company” and the phone number before deciding that it was a just better version of phishing. I didn’t click on anything.
About a month ago I ordered a small jewelry item from a well-known retailer in Scotland. When the item shipped, I received a notice from FedEx that the item had been consigned to them (definitely from FedEx.com, but also another from “Fedex” (note the erroneous capitalization), and the “From” field in the basic email headers listed the sender as Fedex@minayoussef.com. Over the rest of that day I received another dozen or so emails purporting to come from entities such as clothing stores, IT companies, etc., formatted in similar or identical fashion, but obviously fraudulent in origin.
Because this bloom of fraudulent emails started immediately after the shop in Edinburgh contacted FedEx, I worried that my personal information (email address AND possibly my email password) might have been captured by miscreants. I’ve been told by fellow members of an independent Apple Ecosystem listserv that they too have received those messages (from the same bogus domain), which I find a bit reassuring, but I still have a question about Apple’s email security.
I do know that Apple has done things to make its iCloud email platforms more secure, I still wonder about a system where the email password MUST be the same as the password one uses to purchase hardware and software, update computer operating systems and applications, and subscribe to entertainment platforms. Is that a concern to anyone here?
Receiving fraudulent messages sent to your Apple mailbox doesn’t say anything about Apple’s email security.
Anybody can forge any address on an e-mail message and send it from any server.
Now if there was mail where the “Received” headers indicate that it came from your mailbox, that would be reason for concern, although that may be hard to detect, since those messages would probably be sent to other people.
As for why you got all this spam after shopping at one retailer, I would guess that their computer system has been hacked and the crooks got your address from them. Or worse, they may be selling their customer lists to advertisers. After that, it’s open season.
That was my conclusion as well. When I contacted the retailer, the instant reply was “oh, no, that could NEVER happen to us; we contract with IT professionals who make sure we’re protected.” I was tempted to say “just like T-Mobile, and even LastPass?”
But my final question about Apple’s own email security could have been stated more clearly. Actually, I have two questions:
-
Is it good design to have the same identifiers and security (the Apple ID password) for one’s financial transactions with the world’s richest company (buying hardware, obtaining support, subscribing to entertainment services, etc.) and for one’s everyday trips into an environment (email) that’s known widely as far more smarmy than the bar in the very first Star Wars Movie?
-
I’m aware that Apple is promoting “hide my email” addressing, and I don’t really understand how that works. I converse with dozens of people by email every day, and many hundreds over the course of a month or two. What I don’t understand about this new security effort is how my correspondents will know who I am if my email address (the FROM field in my headers) is just gibberish. If, every time I send an email message, Apple creates an encrypted substitute for the “FROM” field unique to that one interaction, won’t that consume ENORMOUS amounts of server space eventually? If, on the other hand, Apple creates a catalog that substitutes the SAME bit of gibberish each time I communicate with a specific email address, doesn’t that risk eventually becoming an easy way to resurrect that chain of correspondence? I’m pretty sure I’m not understanding how this is supposed to work, even with the help of Joe Kissell’s latest Take Control of Apple Mail ebook .
Thanks so much.
Yep. I’ve gotten that kind of runaround from even bigger companies who should know even more.
Like when I got a virus from Microsoft’s Windows update server (proven because I wiped the computer and reinstalled Win95, then reinstalled the virus scanner, which found nothing. Then ran Windows Update, and it immediately detected an infection.) They responded that it’s not possible because they have automatic scanners, so it must somehow be my fault.
And even longer ago when I found a bug in Borland’s Turbo Pascal for Windows compiler, where it generated incorrect machine-language code. I wrote a short 10-line test app and sent it to them, along with the generated code as proof. Their response was that they have no bugs. Then they told me how to change the test program to get the correct results (basically removing the code that triggered their bug).
So I am never surprised when some company, no matter how big or small, reacts to critical problems with flat-out denial.
I would prefer that they provide the option for separate passwords. But I’m not convinced that this is a big problem. If someone manages to log in to your e-mail, that’s a big problem, but I rarely ever hear stories about things like that, and when I do it’s always the result of either phishing or an easily-guessed password. People forging your address on mail sent through other servers is impossible for anyone to prevent.
See What is Hide My Email? - Apple Support
I don’t use this feature, but according to the above page, you request creation of these random e-mail addresses. You give it to whatever people or web sites you like.
I suppose you could generate a new address for every mail message you send, but I don’t think that is the intended use-case. And I wouldn’t recommend it, because legitimate recipients will likely decide that you are a scammer and will block all further communication.
If you generate a new address for each service (web site, store, etc.) you subscribe to, then you should be able to tell who is selling/leaking your address based on where the spam comes from. (I assume you see that address in mail Apple forwards to you.) If you can delete the generated addresses later (I don’t know if you have that option), then it’s a good way to cut-off addresses that have become compromised.
I don’t think the purpose is to hide a chain of correspondence. If you need that level of secrecy, you probably need a different product. I think the goal of Apple’s product is to simply keep to real e-mail address hidden, so identity thieves will have a harder time tracking it to your other accounts, and so you can abandon it (when it gets compromised) without having to abandon your real address.
I guess I should try it out with a few people to whom I send messages routinely, just so I can get a sense of what happens in my own inbox and sent mail box if I use it. I don’t understand very basic things, such as how responses to hidden-address email find their way back to me. I guess I could actually just hide my iCloud mail address in a few messages I send to one or two of my own mail accounts with other providers, or even messages I send to listservs to which I subscribe, but I assume the hiding will result in the listservs’ automated processing rejecting such messages. It seems to me it’s not meant to be a “use it all the time” tool.
I assume Apple sets up mail-forwarding for these addresses. So a message sent to it (to an Apple server) will result in it being forwarded to your iCloud mailbox. If these random addresses are served by the same server that handles the real mailboxes, then this forwarding should be a very quick and simple procedure - just look up the destination mailbox and drop it there.
The web page seems to indicate that when you receive a message via one of these random addresses and then reply to it, the reply will appear to come from that address. This should be no problem if you are using Apple’s mail apps (Mac, iOS or the iCloud web site), but I can’t see how that would work for a third-party mail app, unless you explicitly configure it for each such address. (But maybe there’s an e-mail standard that I’m unaware of that allows this to work in a portable fashion. I haven’t looked.)
That’s not what it’s for. It’s for signing up to services to hide your real email from them, so that if you ever don’t want that service any more, you can just delete the email alias and they have no contact real info for you. Or if they leak that email and you start getting spam to that address, you know they leaked it and can block that address.
While I don’t use this for a “real” service that already knows a lot about me (such as Amazon, which is going to have payment information, my address, and other details), but it’s great for apps that require an email address to set up an account, temporary services you want to test before committing, etc. I use it to sign up for things like fast food apps, etc. which track reward points and give you coupons, games, web apps, and other “throwaway” accounts.
There is someplace where you can go to actually manage these email aliases, but I can never remember where it’s hidden when I need it.
From memory it’s something like Settings > Apple ID > iCloud > Hide My Email
Wonderful that preferences search didn’t bring that up when I searched for “hide” and “email” ![]() . I tried both Mac and iPhone. Bad Apple.
. I tried both Mac and iPhone. Bad Apple.
That’s exactly like the PayPal phishing I documented in the article. It’s not real spam since it’s sent legitimately through PayPal’s systems, but it’s absolutely a scam that should be reported to phishing@paypal.com. I’ve gotten a bunch of these, and I always report them and then delete them without marking them as spam.
I don’t think this is problematic. In fact, I’d suggest that you’re actually reversing the two examples in importance: email is much more important to protect than something you can make purchases with, because control over someone’s email gives them control over many other accounts.
The real key is two-factor authentication, which prevents even a compromised password from being used to break into your account.
And, wherever possible, use 2FA that does not depend on receiving text messages for the response, so a SIM swap scam won’t neutralize that second factor.
I prefer using TOTP code generators, like Google Authenticator (among many that implement the same algorithm). Once initially configured, they generate all their codes locally, without any data exchange with the remote service. So there’s no data to intercept.
As I understand it, Apple’s 2FA is also TOTP (but possibly with a different algorithm). Although it receives notifications from the network, the actual code is generated locally and is not received over the air.
Unfortunately, you don’t always have a choice. Some systems (including banks) insist on sending you SMS text messages or e-mail as a part of their authentication process, which won’t help you if your phone number or mailbox has been compromised.
I have two methods I use for
- Phishing - go hunting and see if you can find a zip file with same name as a folder. If so, download the zip file and have a look through the PHP code. If you find an email address, Sign the f()ckers up for spammy newsletters.
- 419 scams - they invariably have to have a reply to address or try to hide it in the email by putting in spaces and ‘dot’ instead of ‘.’
Sign the f()ckers up for spammy newsletters.
Also, report the phishing to phishtank[dot]com. This way it gets verified and added to antivirus software as malicious. Any spam email, I report to spamcop[dot]org, any suspected virus gets passed through virustotal[dot]com
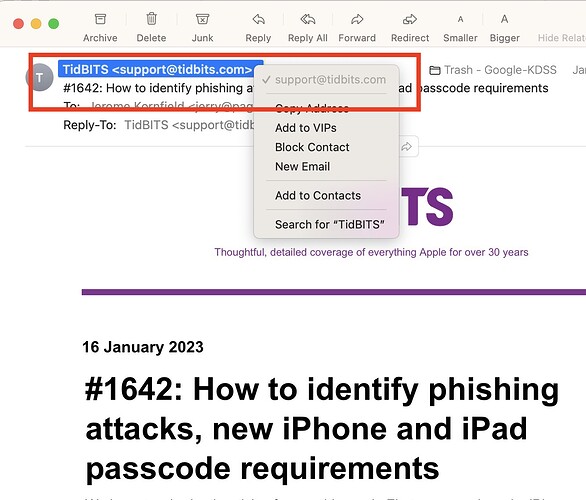
One thing that is about the easiest way to test where the email came from is in the picture.
I try to always go directly to the location if asked to go to “my bank” and log in directly.
Although I would agree that this is the first place to check for phishing, it’s not the last. That field can be easily faked and does not positively identify the source of the message. The full headers showing the where the message was first received need to be examined in order to access the true source of the message.
See also this recent thread:
Quite a lot of information in an e-mail’s headers can be forged, so you need to know what to look for and what to ignore when determining if mail is real or not.
Many times, it’s not possible to know conclusively, in which case you should assume it’s fake and proceed accordingly.
Refusing to click on links from unexpected messages (instead going straight to the source, like your bank, with a URL you know to be valid) is a good practice in general these days.